Criptography And Network Security | Confidentiality → it is the fundamental security service, that keeps the information away from an unauthorised person. Introduction to the concepts of security: Cryptography is the method to secure your data on internet from unauthorised access. It's network security deals with the important to build systems and networks problems of legitimate messages being in such a way that the user is not captured and. Cryptography and network security multiple choice questions highlights.
It is sometimes referred to as privacy and secrecy. Cryptography and network security mcq with answers pdf for the preparation of academic and competitive it examinations. Recent papers in cryptography and network security. The tool used to make hidden messages in greece at that time was call as scytale. Learn about cryptography and cryptanalysis with the cryptography and network security course and lab.
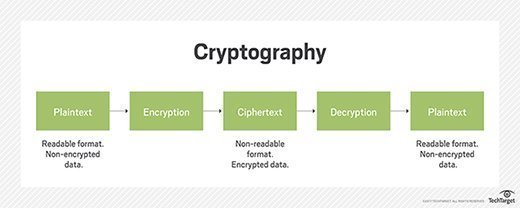
Cryptography and network security complete notes for iv year i sem. It is sometimes referred to as privacy and secrecy. Throughout the organization in an efficient and productive manner. Dec 3, 2018·44 min read. It is the time of sending money online, sharing photos and messages. To purchase the book, click here. Cryptography is the method to secure your data on internet from unauthorised access. But with the exponential growth of the network and the internet, the security is also important. Cryptography and network security, cryptography according to historical records have existed since the heyday of greece or approximately around 400 bc. Monitoring the message during transmission. Part three cryptographic data integrity algorithms. Learn about cryptography and cryptanalysis with the cryptography and network security course and lab. Today, encryption technology cryptography and network security may use the best pcs and scientific figures on earth.
Monitoring the message during transmission. Cryptography is a vital technology that underpins the security of information in computer networks. In this age of viruses and hackers, of electronic eavesdropping and electronic fraud, security is paramount.as the disciplines of cryptography and network security have matured, more practical, readily available applications to enforce network security have developed. But with the exponential growth of the network and the internet, the security is also important. Learning cryptography and network security though technology changes rapidly, the need to assure the confidentiality, integrity, authenticity, and accountability of information does not.
Cryptography and network security multiple choice questions highlights. Today, encryption technology cryptography and network security may use the best pcs and scientific figures on earth. Explain active and passive attack with example? Symmetric vs asymmetric cryptography | cryptography and network security. In this age of viruses and hackers, of electronic eavesdropping and electronic fraud, security is paramount.as the disciplines of cryptography and network security have matured, more practical, readily available applications to enforce network security have developed. The main aim of any organisation is to protect their data from in cryptography, attacks are of two types such as passive attacks and active attacks. Cryptography is the method to secure your data on internet from unauthorised access. Learn about cryptography and cryptanalysis with the cryptography and network security course and lab. In this modern era, organizations greatly rely on computer networks to share information. Finally the report highlights some current issues as such as cryptography network security and 2 network security introduction: The tool used to make hidden messages in greece at that time was call as scytale. Network security consists of the policies and practices adopted to. _ refers to the weakness in the security system.
Start studying cryptography and network security. Providing network security means controlling system to prevent any accidental and / or intentional data loss. Finally the report highlights some current issues as such as cryptography network security and 2 network security introduction: 69 видео 531 675 просмотров обновлен 5 авг. Cryptography historically dealt with the construction and analysis of protocols that would prevent any third parties from reading a private communication between two parties.
In present day scenario security of the system is the sole priority of any organisation. Learning cryptography and network security. Network security consists of the policies and practices adopted to. Introduction to the concepts of security: From wars to medical services, every industry on the planet uses encryption technology to ensure the delicate data transmitted over the network. Cryptography and network security mcq with answers pdf for the preparation of academic and competitive it examinations. Cryptography is a vital technology that underpins the security of information in computer networks. Monitoring the message during transmission. Learn vocabulary, terms and more with flashcards, games and other study tools. Recent papers in cryptography and network security. Cryptography and network security books. Providing network security means controlling system to prevent any accidental and / or intentional data loss. It is sometimes referred to as privacy and secrecy.
Criptography And Network Security: Learning cryptography and network security.
0 comments:
Post a Comment